WORD NEWS
‘Vulkan recordsdata’ leak reveals Putin’s world and home cyberwarfare ways | Cyberwar
The inconspicuous workplace is in Moscow’s north-eastern suburbs. An indication reads: “Enterprise centre”. Close by are trendy residential blocks and a rambling outdated cemetery, house to ivy-covered conflict memorials. The realm is the place Peter the Nice as soon as skilled his mighty military.
Contained in the six-storey constructing, a brand new era helps Russian army operations. Its weapons are extra superior than these of Peter the Nice’s period: not pikes and halberds, however hacking and disinformation instruments.
The software program engineers behind these programs are workers of NTC Vulkan. On the floor, it seems to be like a run-of-the-mill cybersecurity consultancy. Nonetheless, a leak of secret recordsdata from the corporate has uncovered its work bolstering Vladimir Putin’s cyberwarfare capabilities.
Hundreds of pages of secret paperwork reveal how Vulkan’s engineers have labored for Russian army and intelligence companies to help hacking operations, prepare operatives earlier than assaults on nationwide infrastructure, unfold disinformation and management sections of the web.
The corporate’s work is linked to the federal safety service or FSB, the home spy company; the operational and intelligence divisions of the armed forces, often called the GOU and GRU; and the SVR, Russia’s international intelligence organisation.
One doc hyperlinks a Vulkan cyber-attack device with the infamous hacking group Sandworm, which the US authorities mentioned twice brought about blackouts in Ukraine, disrupted the Olympics in South Korea and launched NotPetya, probably the most economically harmful malware in historical past. Codenamed Scan-V, it scours the web for vulnerabilities, that are then saved to be used in future cyber-attacks.
One other system, often called Amezit, quantities to a blueprint for surveilling and controlling the web in areas below Russia’s command, and likewise permits disinformation by way of faux social media profiles. A 3rd Vulkan-built system – Crystal-2V – is a coaching program for cyber-operatives within the strategies required to carry down rail, air and sea infrastructure. A file explaining the software program states: “The extent of secrecy of processed and saved data within the product is ‘High Secret’.”
The Vulkan recordsdata, which date from 2016 to 2021, had been leaked by an nameless whistleblower angered by Russia’s conflict in Ukraine. Such leaks from Moscow are extraordinarily uncommon. Days after the invasion in February final 12 months, the supply approached the German newspaper Süddeutsche Zeitung and mentioned the GRU and FSB “disguise behind” Vulkan.
“Folks ought to know the hazards of this,” the whistleblower mentioned. “Due to the occasions in Ukraine, I made a decision to make this data public. The corporate is doing unhealthy issues and the Russian authorities is cowardly and unsuitable. I’m indignant in regards to the invasion of Ukraine and the horrible issues which might be occurring there. I hope you need to use this data to point out what is going on behind closed doorways.”
The supply later shared the information and additional data with the Munich-based investigative startup Paper Path Media. For a number of months, journalists working for 11 media shops, together with the Guardian, Washington Put up and Le Monde, have investigated the recordsdata in a consortium led by Paper Path Media and Der Spiegel.
5 western intelligence companies confirmed the Vulkan recordsdata look like genuine. The corporate and the Kremlin didn’t reply to a number of requests for remark.
The leak incorporates emails, inner paperwork, undertaking plans, budgets and contracts. They provide perception into the Kremlin’s sweeping efforts within the cyber-realm, at a time when it’s pursuing a brutal conflict towards Ukraine. It isn’t recognized whether or not the instruments constructed by Vulkan have been used for real-world assaults, in Ukraine or elsewhere.
However Russian hackers are recognized to have repeatedly focused Ukrainian laptop networks; a marketing campaign that continues. Since final 12 months’s invasion, Moscow’s missiles have hit Kyiv and different cities, destroying essential infrastructure and leaving the nation at the hours of darkness.
Analysts say Russia can also be engaged in a continuous battle with what it perceives as its enemy, the west, together with the US, UK, EU, Canada, Australia and New Zealand, all of which have developed their very own categorised cyber-offensive capabilities in a digital arms race.
Some paperwork within the leak comprise what look like illustrative examples of potential targets. One incorporates a map exhibiting dots throughout the US. One other incorporates the small print of a nuclear energy station in Switzerland.
One doc reveals engineers recommending Russia add to its personal capabilities through the use of hacking instruments stolen in 2016 from the US Nationwide Safety Company and posted on-line.
John Hultquist, the vice-president of intelligence evaluation on the cybersecurity agency Mandiant, which reviewed picks of the fabric on the request of the consortium, mentioned: “These paperwork counsel that Russia sees assaults on civilian essential infrastructure and social media manipulation as one and the identical mission, which is basically an assault on the enemy’s will to battle.”
What’s Vulkan?
Vulkan’s chief govt, Anton Markov, is a person of center years, with cropped hair and darkish baggage across the eyes. Markov based Vulkan (that means volcano in English) in 2010, with Alexander Irzhavsky. Each are graduates of St Petersburg’s army academy and have served with the military up to now, rising to captain and main respectively. “That they had good contacts in that course,” one former worker mentioned.

The corporate is a part of Russia’s military-industrial complicated. This subterranean world encompasses spy companies, industrial corporations and better training establishments. Specialists resembling programmers and engineers transfer from one department to a different; secret state actors rely closely on non-public sector experience.
Vulkan launched at a time when Russia was quickly increasing its cyber-capabilities. Historically, the FSB took the lead in cyber affairs. In 2012 Putin appointed the formidable and energetic Sergei Shoigu as defence minister. Shoigu – who’s accountable for Russia’s conflict in Ukraine – needed his personal cyber-troops, reporting on to him.
From 2011 Vulkan obtained particular authorities licences to work on categorised army initiatives and state secrets and techniques. It’s a mid-sized tech firm, with greater than 120 employees – about 60 of whom are software program builders. It isn’t recognized what number of non-public contractors are granted entry to such delicate initiatives in Russia, however some estimates counsel it’s not more than a few dozen.
Vulkan’s company tradition is extra Silicon Valley than spy company. It has a employees soccer workforce, and motivational emails with health ideas and celebrations of worker birthdays. There may be even an upbeat slogan: “Make the world a greater place” seems in a shiny promotional video.
Vulkan says it specialises in “data safety”; formally, its clients are huge Russian state corporations. They embody Sberbank, the nation’s largest financial institution; the nationwide airline Aeroflot; and Russian railways. “The work was enjoyable. We used the newest applied sciences,” mentioned one former worker who ultimately left after they grew disillusioned with the job.“The folks had been actually intelligent. And the cash was good, nicely above the standard price.”
In addition to technical experience, these beneficiant salaries purchased the expectation of discretion. Some employees are graduates of Bauman Moscow State Technical College, which has an extended historical past of feeding recruits to the defence ministry. Workflows are organised on rules of strict operational secrecy, with employees by no means being instructed what different departments are engaged on.
The agency’s ethos is patriotic, the leak suggests. On New Yr’s Eve in 2019 an worker created a lighthearted Microsoft Excel file with Soviet army music and an image of a bear. Alongside it had been the phrases: “APT Magma Bear”. The reference is to Russian state hacking teams resembling Cozy Bear and Fancy Bear, and seems to level to Vulkan’s personal shadowy actions.
5 months later, Markov reminded his staff of Victory Day, a 9 Could vacation celebrating the Crimson Military’s defeat of Nazi Germany in 1945. “It is a important occasion within the historical past of our nation,” he instructed employees. “I grew up on movies in regards to the conflict and had the great fortune to speak with veterans and to take heed to their tales. These folks died for us, so we will dwell in Russia.”
One in all Vulkan’s most far-reaching initiatives was carried out with the blessing of the Kremlin’s most notorious unit of cyberwarriors, often called Sandworm. Based on US prosecutors and western governments, over the previous decade Sandworm has been answerable for hacking operations on an astonishing scale. It has carried out quite a few malign acts: political manipulation, cyber-sabotage, election interference, dumping of emails and leaking.
Sandworm disabled Ukraine’s energy grid in 2015. The next 12 months it took half in Russia’s brazen operation to derail the US presidential election. Two of its operatives had been indicted for distributing emails stolen from Hillary Clinton’s Democrats utilizing a faux persona, Guccifer 2.0. Then in 2017 Sandworm purloined additional information in an try to affect the result of the French presidential vote, the US says.
That very same 12 months the unit unleashed probably the most consequential cyber-attack in historical past. Operatives used a bespoke piece of malware known as NotPetya. Starting in Ukraine, NotPetya quickly unfold throughout the globe. It knocked offline delivery corporations, hospitals, postal programs and pharmaceutical producers – a digital onslaught that spilled over from the digital into the bodily world.
The Vulkan recordsdata make clear a bit of digital equipment that might play a component within the subsequent assault unleashed by Sandworm.

A system ‘constructed for offensive functions’
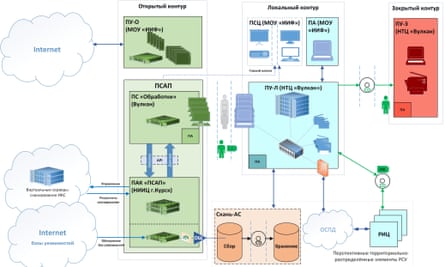
A particular unit inside the GRU’s “major centre for particular applied sciences”, Sandworm is understood internally by its subject quantity 74455. This code seems within the Vulkan recordsdata as an “approval social gathering” on a technical doc. It describes a “information trade protocol” between an apparently pre-existing military-run database containing intelligence about software program and {hardware} weaknesses, and a brand new system that Vulkan had been commissioned to assist construct: Scan-V.
Hacking teams resembling Sandworm penetrate laptop programs by first searching for weak spots. Scan-V helps that course of, conducting automated reconnaissance of potential targets around the globe in a hunt for doubtlessly weak servers and community gadgets. The intelligence is then saved in a knowledge repository, giving hackers an automatic technique of figuring out targets.
Gabby Roncone, one other knowledgeable with the cybersecurity firm Mandiant, gave the analogy of scenes from outdated army motion pictures the place folks place “their artillery and troops on the map. They wish to perceive the place the enemy tanks are and the place they should strike first to interrupt via the enemy strains,” she mentioned.
The Scan undertaking was commissioned in Could 2018 by the Institute of Engineering Physics, a analysis facility within the Moscow area carefully related to the GRU. All particulars had been categorised. It isn’t clear whether or not Sandworm was an meant consumer of the system, however in Could 2020 a workforce from Vulkan visited a army facility in Khimki, the identical metropolis on the outskirts of Moscow the place the hacking unit is predicated, to check the Scan system.
“Scan is unquestionably constructed for offensive functions. It suits comfortably into the organisational construction and the strategic method of the GRU,” one analyst mentioned after reviewing the paperwork. “You don’t discover community diagrams and design paperwork like this fairly often. It actually could be very intricate stuff.”
The leaked recordsdata comprise no details about Russian malicious code, or malware, used for hacking operations. However an analyst with Google mentioned that in 2012 the tech agency linked Vulkan to an operation involving a malware often called MiniDuke. The SVR, Russia’s international intelligence company, used MiniDuke in phishing campaigns. The leak reveals that an undercover a part of the SVR, army unit 33949, contracted Vulkan to work on a number of initiatives. The corporate codenamed its consumer “sanatorium” and “dispensary”.
Web management, surveillance and disinformation
In 2018, a workforce of Vulkan workers travelled south to attend the official testing of a sweeping program enabling web management, surveillance and disinformation. The assembly came about on the FSB-linked Rostov-on-Don Radio Analysis Institute. It subcontracted Vulkan to assist in the creation of the brand new system, dubbed Amezit, which was additionally linked within the recordsdata to the Russian army.
“Lots of people labored on Amezit. Time and cash was invested,” a former worker recalled. “Different corporations had been concerned as nicely, probably as a result of the undertaking was so huge and necessary.”
Vulkan performed a central position. It received an preliminary contract to construct the Amezit system in 2016 however paperwork counsel components of Amezit had been nonetheless being improved by Vulkan engineers nicely into 2021, with plans for additional growth in 2022.
One a part of Amezit is domestic-facing, permitting operatives to hijack and take management of the web if unrest breaks out in a Russian area, or the nation positive aspects a stronghold over territory in a rival nation state, resembling Ukraine. Web visitors deemed to be politically dangerous might be eliminated earlier than it has an opportunity to unfold.
A 387-page inner doc explains how Amezit works. The army wants bodily entry to {hardware}, resembling cell phone towers, and to wi-fi communications. As soon as they management transmission, visitors might be intercepted. Army spies can determine folks looking the net, see what they’re accessing on-line, and monitor data that customers are sharing.
Since final 12 months’s invasion, Russia has arrested anti-war protesters and handed punitive legal guidelines to forestall public criticism of what Putin calls a “particular army operation”. The Vulkan recordsdata comprise paperwork linked to an FSB operation to observe social media utilization inside Russia on a huge scale, utilizing semantic evaluation to identify “hostile” content material.
Based on a supply aware of Vulkan’s work, the agency developed a bulk assortment program for the FSB known as Fraction. It combs websites resembling Fb or Odnoklassniki – the Russian equal – searching for key phrases. The goal is to determine potential opposition figures from open supply information.
Vulkan employees often visited the FSB’s data safety centre in Moscow, the company’s cyber-unit, to seek the advice of on the key program. The constructing is subsequent to the FSB’s Lubyanka headquarters and a bookshop; the leak reveals the unit’s spies had been jokingly nicknamed “book-lovers”.
The event of those secret packages speaks to the paranoia on the coronary heart of Russia’s management. It’s fearful of avenue protests and revolution of the type seen in Ukraine, Georgia, Kyrgyzstan and Kazakhstan. Moscow regards the web as an important weapon in sustaining order. At house, Putin has eradicated his opponents. Dissidents have been locked up; critics resembling Alexei Navalny poisoned and jailed.
It’s an open query as as to if Amezit programs have been utilized in occupied Ukraine. In 2014 Russia covertly swallowed the jap cities of Donetsk and Luhansk. Since final 12 months, it has taken additional territory and shut down Ukrainian web and cellular providers in areas it controls. Ukrainian residents have been compelled to attach by way of Crimea-based telecoms suppliers, with sim playing cards handed out in “filtration” camps run by the FSB.
Nonetheless, reporters had been capable of monitor down real-world exercise carried out by faux social media accounts linked to Vulkan as a part of a sub-system of Amezit, codenamed PRR.
The Kremlin was already recognized to have made use of its disinformation manufacturing unit, the St Petersburg-based Web Analysis Company, which has been placed on the US sanctions listing. The billionaire Yevgeny Prigozhin, Putin’s shut ally, is behind the mass manipulation operation. The Vulkan recordsdata present how the Russian army employed a personal contractor to construct comparable instruments for automated home propaganda.
This Amezit sub-system permits the Russian army to hold out large-scale covert disinformation operations on social media and throughout the web, via the creation of accounts that resemble actual folks on-line, or avatars. The avatars have names and stolen private pictures, that are then cultivated over months to curate a practical digital footprint.
The leak incorporates screenshots of faux Twitter accounts and hashtags utilized by the Russian army from 2014 till earlier this 12 months. They unfold disinformation, together with a conspiracy concept about Hillary Clinton and a denial that Russia’s bombing of Syria killed civilians. Following the invasion of Ukraine, one Vulkan-linked faux Twitter account posted: “Glorious chief #Putin”.
One other Vulkan-developed undertaking linked to Amezit is way extra threatening. Codenamed Crystal-2V, it’s a coaching platform for Russian cyber-operatives. Able to permitting simultaneous use by as much as 30 trainees, it seems to simulate assaults towards a variety of important nationwide infrastructure targets: railway strains, electrical energy stations, airports, waterways, ports and industrial management programs.
An ongoing safety threat?
The intrusive and harmful nature of the instruments that Vulkan has been employed to construct elevate troublesome questions for software program builders who’ve labored on these initiatives. Can they be described as cyber-mercenaries? Or Russian spies? Some nearly definitely are. Others are maybe mere cogs in a wider machine, performing necessary engineering duties for his or her nation’s cyber-military complicated.
Till Russia’s invasion of Ukraine in 2022, Vulkan employees overtly travelled to western Europe, visiting IT and cybersecurity conferences, together with a gathering in Sweden, to mingle with delegates from western safety corporations.
Former Vulkan graduates now dwell in Germany, Eire and different EU nations. Some work for world tech companies. Two are at Amazon Net Companies and Siemens. Siemens declined to touch upon particular person workers however mentioned it took such questions “very significantly”. Amazon mentioned it carried out “strict controls” and that defending buyer information was its “high precedence”.
It’s unclear if former Vulkan engineers now within the west pose a safety threat, and whether or not they have come to the eye of western counter-intelligence companies. Most, it could appear, have family again in Russia, a vulnerability recognized to have been utilized by the FSB to stress Russian professionals overseas to collaborate.
Contacted by a reporter, one ex-staffer expressed remorse at having helped Russia’s army and home spy company. “To start with it wasn’t clear what my work could be used for,” they mentioned. “Over time I understood that I couldn’t stick with it, and that I didn’t wish to help the regime. I used to be afraid one thing would occur to me, or I’d find yourself in jail.”
There have been huge dangers, too, for the nameless whistleblower behind the Vulkan recordsdata. The Russian regime is understood for looking down these it regards as traitors. Of their transient trade with a German journalist, the leaker mentioned they had been conscious that giving delicate data to international media was harmful. However they’d taken life-changing precautions. That they had left their earlier life behind, they mentioned, and now existed “as a ghost”.
Trending
-
Bank and Cryptocurrency12 months ago
Cheap Car Insurance Rates Guide to Understanding Your Options, Laws, and Discounts
-
Bank and Cryptocurrency12 months ago
Why Do We Need an Insurance for Our Vehicle?
-

 entertainement6 months ago
entertainement6 months agoHOUSE OF FUN DAILY GIFTS
-
WORD NEWS1 year ago
Swan wrangling and ‘steamy trysts’: the weird lives and jobs of the king’s entourage | Monarchy